
Modern DeFi protocols face a persistent threat: MEV (Maximal Extractable Value) exploits that undermine fairness and efficiency in modular auctions. As blockchains evolve toward modular architectures, the attack surface for sophisticated MEV strategies has expanded, making deterministic MEV protection a critical focus for developers and protocol designers. The latest innovations in transaction ordering and cryptographic obfuscation are fundamentally reshaping how blockspace markets defend against value extraction exploits.

Why Deterministic Ordering Is Essential for Modular Auction Security
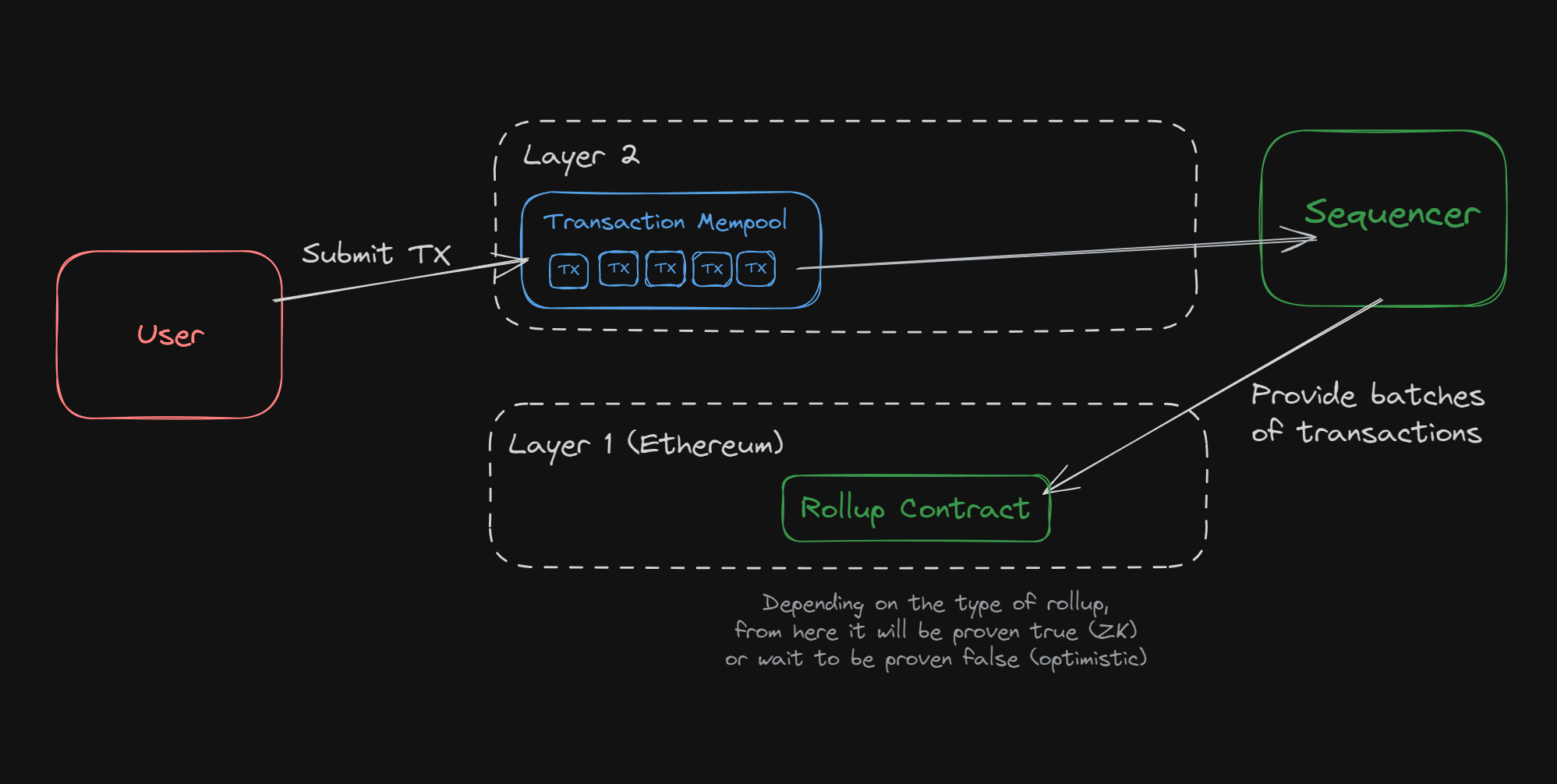
Traditional block production gives miners or validators significant discretion over transaction sequencing. This flexibility is routinely exploited through front-running, sandwich attacks, and other forms of MEV that can erode user trust and protocol stability. In modular auctions, where orderflow is aggregated across multiple domains or rollups, these risks multiply, making modular auction security a non-negotiable requirement.
EIP-7956 exemplifies the new wave of deterministic solutions. By introducing block-level randomness to sort transactions (via XOR-ing hashes with slot-specific entropy), it ensures that while the final order is fixed and transparent post-slot, it remains unpredictable beforehand. This approach sharply reduces reorder-based MEV opportunities without sacrificing composability or throughput.
The shift to deterministic ordering isn’t just about stopping attacks; it’s about restoring credible neutrality to the very foundation of decentralized finance.
Cutting-Edge Mechanisms: Encrypted Mempools and Collaborative Block Building
Beyond consensus-layer randomness, projects like Radius and Algoryte are pioneering encrypted mempool designs. These systems prevent sequencers from accessing transaction details until after pre-confirmations are issued, neutralizing both censorship and sandwiching exploits at the infrastructure level. In practice, this means users can submit sealed-bid transactions, revealed only once included in a block, effectively closing off avenues for predatory searchers.
dYdX’s architecture takes another path: validators collectively vote on which orders enter a batch before any proposer can influence sequencing. The proposer then runs an auction over this majority-backed set, ensuring no single party can manipulate execution order for personal gain (source). Such collaborative models are gaining momentum as practical blueprints for MEV exploits prevention.
The Current State of DeFi Attack Mitigation Techniques
The ecosystem’s response to MEV has become more sophisticated as adversaries adapt to new defenses. Leading protocols now combine cryptographic techniques with incentive-aligned mechanism design:
Top Deterministic MEV Protection Methods in DeFi
-
EIP-7956: Block-Level Randomness Transaction OrderingThis Ethereum Improvement Proposal enforces deterministic transaction ordering by XOR-ing transaction hashes with fresh block-level randomness, making the final order unpredictable until block creation. This approach significantly reduces reorder-based MEV, such as sandwich and front-running attacks.
-
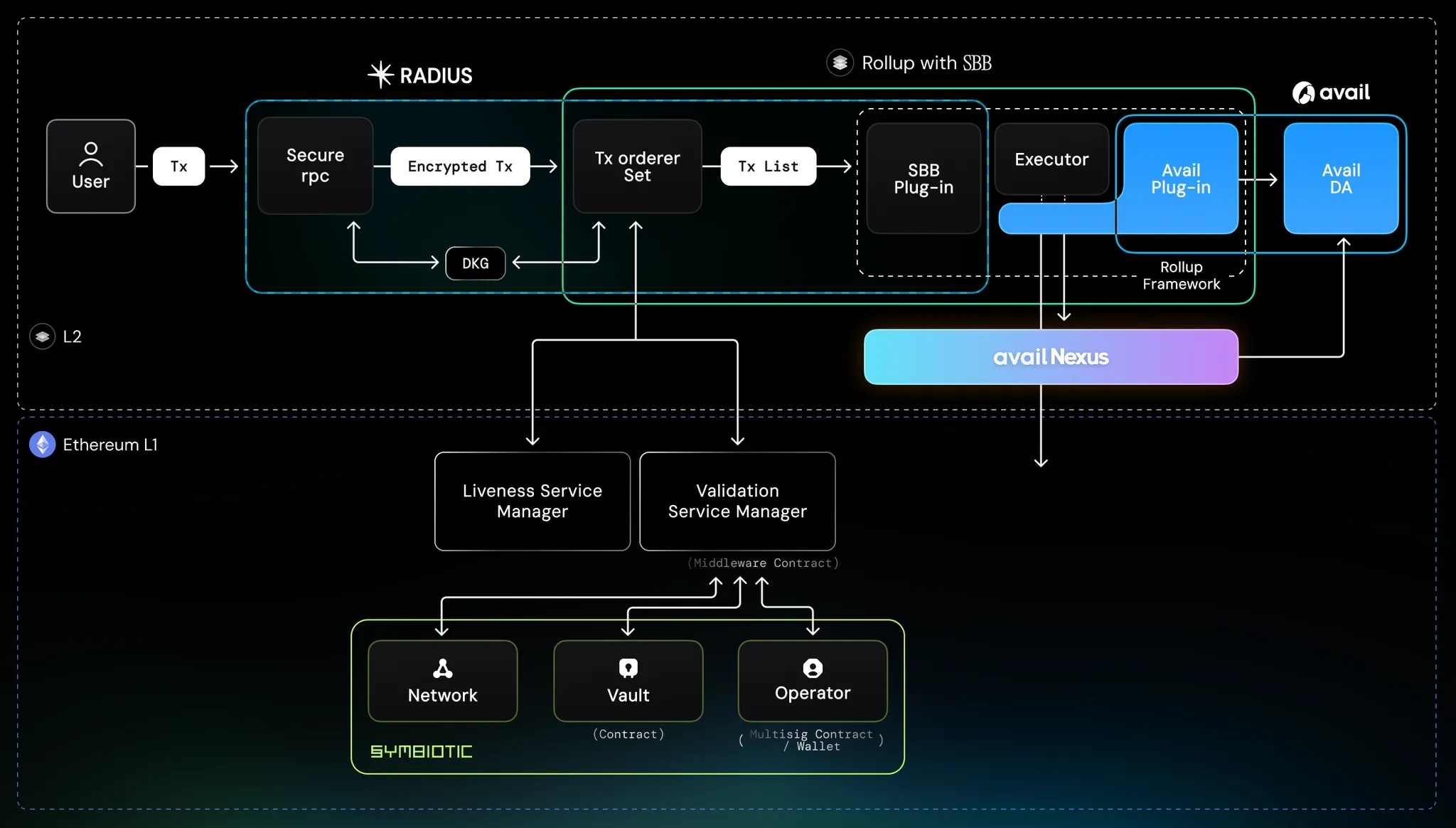
Radius: Decentralized Rollup Sequencers with Encrypted MempoolsRadius introduces encrypted mempools for rollup sequencers, ensuring transactions remain hidden until pre-confirmation. This prevents sequencer-based censorship and reordering, effectively mitigating MEV exploits in modular auction environments.
-
Algoryte: MEV-Resistant InfrastructureAlgoryte implements sealed-bid transaction submission and deterministic ordering across multiple chains. Transactions are encrypted and only revealed post-confirmation, eliminating opportunities for front-running and sandwich attacks.
-

dYdX: Collaborative Block Building and Batch AuctionsdYdX’s architecture uses validator voting and frequent batch auctions to neutralize the effects of transaction sequencing. Orders are included by majority vote before block production, ensuring fair execution and robust MEV protection.
This multi-layered approach not only raises the technical bar for attackers but also makes blockchain transaction safety measurable, a crucial step toward institutional adoption and mainstream confidence.
As deterministic MEV protection matures, it’s clear that the industry is moving beyond ad hoc patchwork to systemic, protocol-level solutions. Innovations like sealed-bid auctions and randomized transaction ordering are no longer theoretical, they’re being deployed on live networks, setting new standards for modular auction security. The result is a paradigm where fairness is not just promised but cryptographically enforced.
Importantly, these advances do not come at the expense of performance or composability. With approaches such as EIP-7956, transaction throughput and user experience remain uncompromised, while the attack surface for reorder-based MEV is dramatically reduced. Similarly, encrypted mempools pioneered by teams like Algoryte provide a robust shield against information leakage without fragmenting liquidity or introducing operational overhead.
What’s Next for Modular MEV Auctions?
The next phase of modular auction development will likely be defined by three core trends:
Top 5 Trends in Deterministic MEV Protection
-

EIP-7956: Block-Level Randomness for Transaction OrderingThis Ethereum Improvement Proposal enforces deterministic transaction ordering by XOR-ing transaction hashes with slot-specific randomness, making reordering exploits like sandwich and front-running attacks significantly harder.
-
Encrypted Mempools and Decentralized Sequencers (Radius)Radius introduces encrypted mempools to modular rollups, ensuring sequencers cannot censor or reorder transactions, thereby enhancing user protection against MEV attacks.
-

Algoryte’s Cross-Chain MEV-Resistant InfrastructureAlgoryte implements sealed-bid transaction submission and deterministic ordering, preventing transaction contents from being revealed before block confirmation and reducing front-running risks across multiple blockchains.
-

dYdX: Collaborative Block Building and Batch AuctionsdYdX’s architecture leverages validator voting and frequent batch auctions, neutralizing transaction sequencing effects and minimizing opportunities for MEV extraction in decentralized trading.
-
Deterministic Transaction Fee Mechanism DesignEmerging fee mechanisms, such as SAKA, are deterministic and sybil-proof, aligning incentives for users, searchers, and block producers while reducing MEV by removing time-sensitive execution paths.
First, expect broader adoption of encrypted mempool infrastructure across both L1s and modular rollups. Second, look for more protocols to experiment with collaborative block building and batch auction designs that align validator incentives with user safety. Third, as regulatory scrutiny intensifies, transparent and auditable ordering mechanisms will become table stakes for any protocol seeking institutional capital.
Ultimately, deterministic MEV protection is about more than neutralizing today’s exploits, it’s about future-proofing decentralized markets against tomorrow’s adversaries. As these technologies proliferate, users and developers alike can expect a landscape where value extraction is governed by code rather than opportunism.
The rapid progress in deterministic ordering and cryptographic defense mechanisms signals a turning point in DeFi attack mitigation. Protocols that embrace these innovations will not only safeguard their users but also set the benchmark for trustless finance in an increasingly modular world.






